
In the stretch of a few days, two municipal water facilities that serve more than 2 million residents in parts of Pennsylvania and Texas have reported network security breaches that have hamstrung parts of their business or operational processes.
In response to one of the attacks, the Municipal Water Authority of Aliquippa in western Pennsylvania temporarily shut down a pump providing drinking water from the facility’s treatment plant to the townships of Raccoon and Potter, according to reporting by the Beaver Countian. A photo the Water Authority provided to news outlets showed the front panel of a programmable logic controller—a toaster-sized box often abbreviated as PLC that’s used to automate physical processes inside of industrial settings—that displayed an anti-Israeli message. The PLC bore the logo of the manufacturer Unitronics. A sign above it read “Primary PLC.”
WWS facilities in the crosshairs
The Cybersecurity and Infrastructure Security Administration on Tuesday published an advisory that warned of recent attacks compromising Unitronics PLCs used in Water and Wastewater Systems, which are often abbreviated as WWSes. Although the notice didn’t identify any facilities by name, the account of one hack was almost identical to the one that occurred inside the Aliquippa facility.
“Cyber threat actors are targeting PLCs associated with WWS facilities, including an identified Unitronics PLC, at a US water facility,” CISA officials wrote. “In response, the affected municipality’s water authority immediately took the system offline and switched to manual operations—there is no known risk to the municipality’s drinking water or water supply.”
Water Authority officials told reporters the hacked PLC regulates pressure to elevated regions and was housed in what’s known as a booster station that served Raccoon and Potter. As soon as the PLC was hacked, the booster station sent an alarm to operators who then took the system offline and took manual control. They said there was never a threat to the availability of water to the 6,615 customers the facility serves.
A second hack hitting the North Texas Municipal Water District came to light on Monday after a ransomware group tracked as DAIXIN added the district, abbreviated as NTMWD, to its leak site. The post said the group has stolen sensitive data contained in 33,844 files. A text file that accompanied the post showed what appeared to be an extensive file directory tree of the network belonging to the NTMWD.
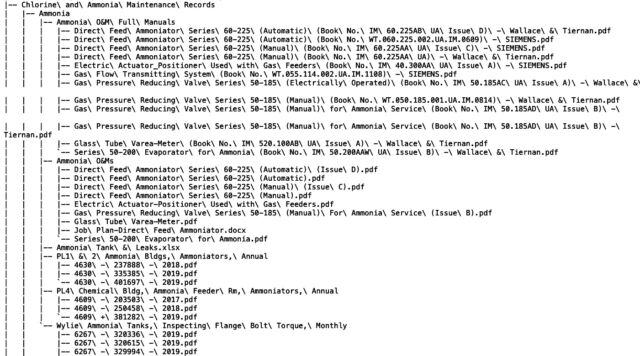
“The North Texas Municipal Water District (NTMWD) recently detected a cybersecurity incident affecting our business computer network,” an official wrote in an email. “Most of our business network has been restored. Our core water, wastewater, and solid waste services to our Member Cities and Customers have not been impacted by this incident, and we continue to provide those services as usual.” The official went on to say that phone systems remained offline. The district has engaged third-party forensic investigators to probe the extent of the breach.
While the network intrusion didn’t come to light until Monday, NTMWD first notified residents of a phone outage on November 12. The official didn’t say when the breach occurred. NTMWD serves 2.2 million people across 2,200 square miles.
DAIXIN was first spotted in June 2022. The group, which has been actively tracked by both CISA and the Water Information Sharing and Analysis Center, has successfully targeted a wide range of industries including health care, aerospace, automotive, and packaged foods.
Less is known about Cyber Aveng3rs, the group claiming responsibility for the hack on the Municipal Water Authority of Aliquippa. It may be the same group known as Cyber Av3ngers or connected to Cyber Av3ngers, which has ties to a group Microsoft has linked to the Iranian-government-backed Moses group.
It’s tempting to think that the hacks of two different water facilities coming to light within a few days signals an escalation. It’s easier to bear in mind that water facilities are notoriously underfunded and employ IT staff who receive little training and resources and are underpaid. Either way, the attacks should serve as a wake up call to political leaders at every level of government that critical infrastructure is vulnerable to hacking and will remain that way until they make the necessary investments.
reader comments
37